Our approach for delivering a complete IoT assessment

Internet of Things (IoT) Security
Thanks to the diversified skills of its consultants and a wide range of services that we offer, we are able to support customers during the evaluation of their IoT infrastructure, perform all necessary tests to find and validate potentially security vulnerabilities and then prioritize detected issues in order to fix them.
The following is our approach for delivering a complete IoT assessment:
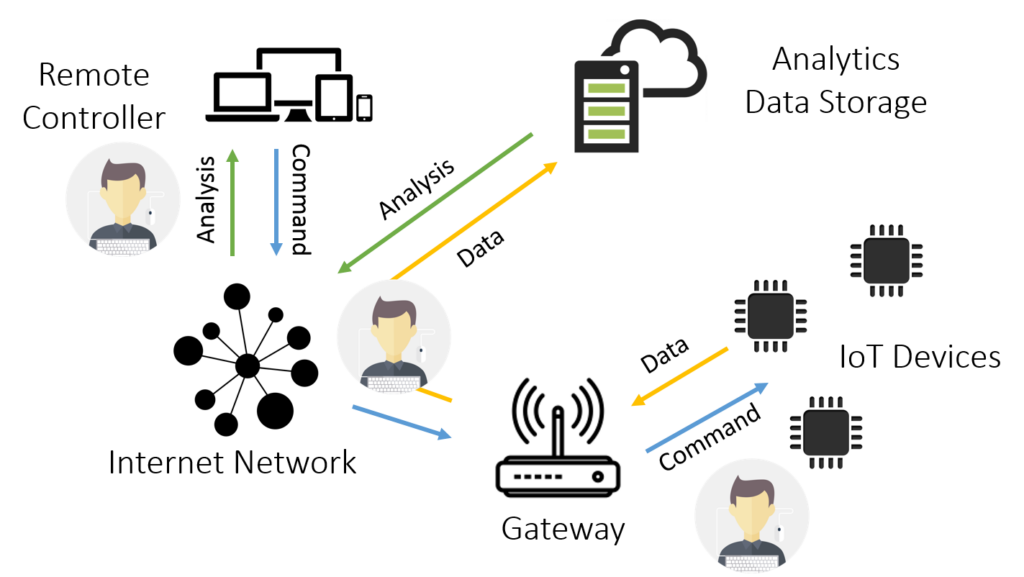
A complex stack of different technologies composes the majority of IoT ecosystems so firstly, IMQ Minded Security performs a high-level assessment to understand where the IoT devices are standing inside the customer’s network, how they interact and share information with other devices and what kind of information they send outside the customer’s network.
The aim of this activity is to identify all the possible attack surfaces (as defined by OWASP) that an attacker could exploit to steal data, cause denial of services or, in the worst case scenario, take full control of the devices.
Once the assessment phase is complete, it is possible to highlight all the security-related points of interest regarding the customer’s IoT environment and then evaluate if it is necessary to focus attention on only a single part of the environment or review the integration between different components.
At this point IMQ Minded Security can help the customer to plan and prioritize different specific activities such as:
- Mobile Application Security Assessment. If the IoT devices can be controlled or interact with a mobile application (Android or iOS), our company can perform security assessment on it and identify all the issues related to this kind of remote controller.
- Device Security Assessment. We can perform a black box assessment against the device while inside a specific testing network in order to better understand device behavior and identify possible data leakage. It is also possible to perform a white box analysis and the source code review of device firmware.
- Web Application Penetration Test (WAPT). It is important to test all the Web Applications that, in many parts of the IoT environment, can collect data or send commands to the devices. For example, it is possible to perform a WAPT against the cloud application used by the employee to control and monitor remote devices or test the device built-in web application.
- Network Penetration Test (NPT). The best way to find communication protocol vulnerabilities or networking misconfiguration is to perform a wide network assessment aimed at highlighting any potential side channels, data leakages or insufficient encryption inside the customer’s IoT ecosystem.
Want more? Read our blog posts on pentesting IoT devices